Welcome to the exciting world of threat models! Or as I like to call it, the rollercoaster ride of paranoia and protection.
Have you ever felt like your computer was out to get you? Or that your phone was secretly plotting against you? Well, my friend, you're not alone. In today's world, cyber threats are as common as business majors. And just like you wouldn't leave your house without pants (I hope), you shouldn't leave your digital life unprotected.
But don't worry, we're here to guide you through the mazes of threat models. So sit back, grab some popcorn, and let's dive into the wild and wacky world of cybersecurity!
1) What is a threat model?
The purpose of a threat model is to assess the risks and determine appropriate security measures to protect against potential threats. It's like preparing for a heist with a team of experts, except you're protecting your digital assets instead of stealing them.
In less technical terms: let’s say you’re trying to protect a treasure, threat modeling is imagining all the ways someone might try to take your treasure and coming up with a plan to stop them. So, you might decide to put a lock on the window and make the ground really hard so no one can dig through it.
In the same way, when we use the internet or our phones, we want to keep our information safe from bad people who might try to take it. So, we think about all the ways they might try to take it and come up with a plan to stop them. It's like having a secret treasure that you want to protect from anyone who might try to take it.

2) Why should you threat model?
You should threat model because you want to keep your treasure safe. Just like how you don't want anyone to take your favorite toy or snack, you don't want anyone to take your information or things you have on your phone or computer. So, by threat modeling, you can think of all the ways someone might try to take your treasure and come up with a plan to stop them.
Threat modeling is like the bodyguard you never knew you needed. With the rise of cybercrime, from phishing attacks and malware infections to hacking attempts and data breaches, the potential for security breaches is always present. But with threat modeling, you can be like Liam Neeson in Taken: proactively identifying and mitigating potential security risks before they are exploited.
Threat modeling can also help organizations meet regulatory requirements and industry standards. It's like passing the ultimate test to become a certified security expert. Many regulations and standards require organizations to undertake a threat modeling process to ensure that appropriate security measures are in place to protect against potential threats. Failure to do so can result in fines, legal action, and reputational damage. And nobody wants to be the laughing stock of the cybersecurity community.
Additionally, threat modeling is a nice way for you to set your own goals and be independent when it comes to privacy and security, as you will know your priorities and you will be able to focus on achieving them.
3) How can I create my own threat model?
There is countless ways to make a threat model, it all depends on who you are and what you want to protect.
For individuals we recommend the Techlore Dispatch approach because we found that it is by far the easiest and most concrete way to develop a threat model:
Get a sheet of paper, draw a 3x3 table, and add categories for each case:
A good starting point is People, Companies and Governments on the X axis, Security, Privacy and anonymity on the Y axis.
If you don’t know the difference between Privacy, Security and Anonymity we recommend studying up before making a threat model by reading our posts on each of the topics:
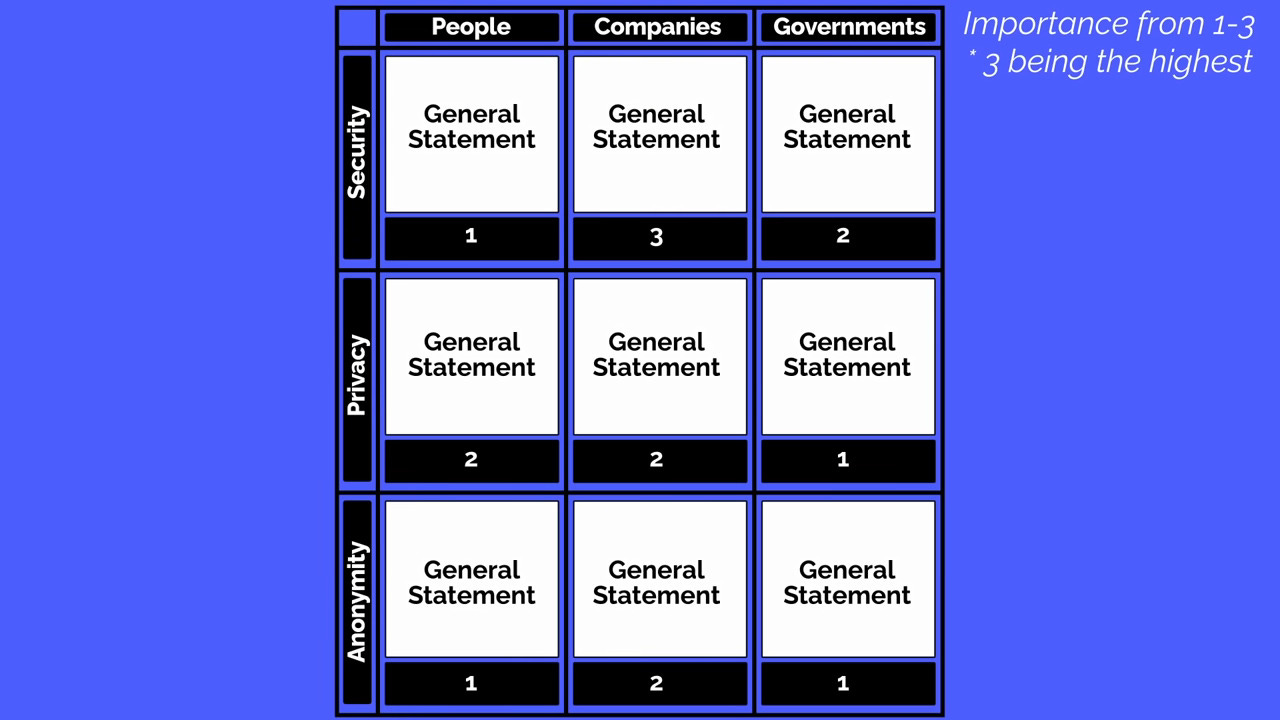
Rate the overall importance of each category ranging from 1 to 3 (with 3 being the highest)
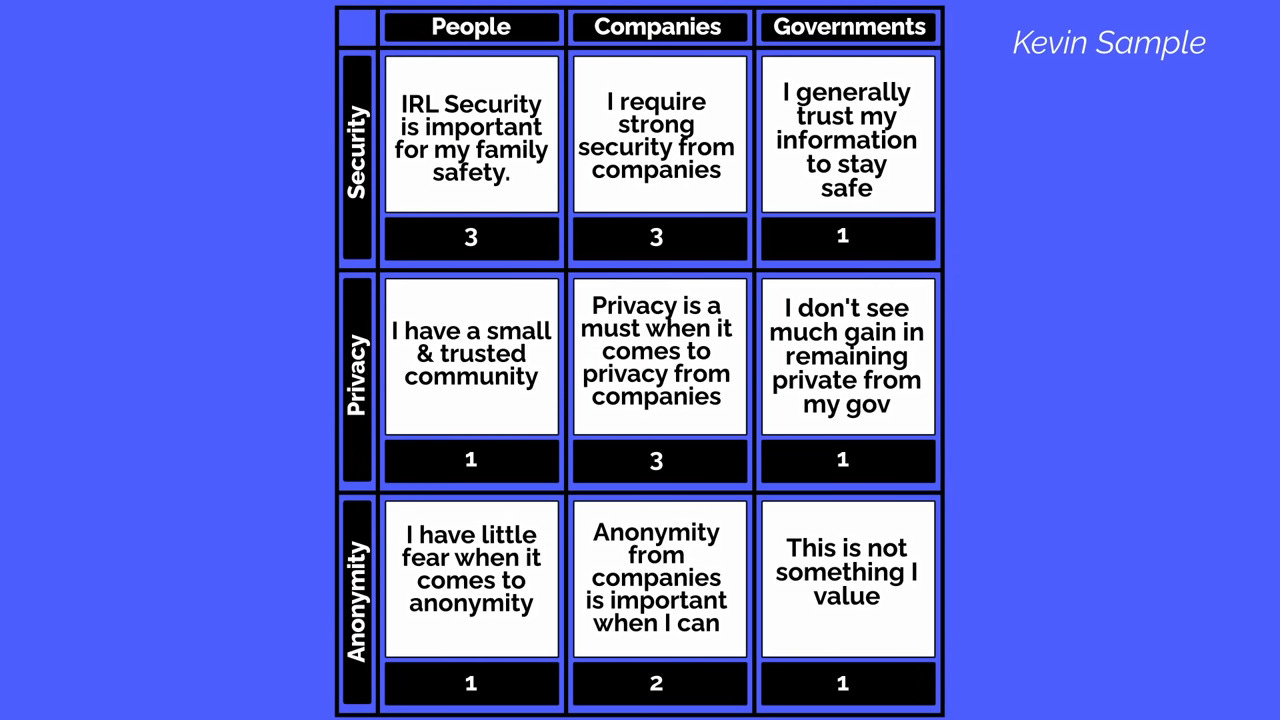
Add a a general statement for each case describing what do you want to protect and why.
You should now have something that looks a little like this:
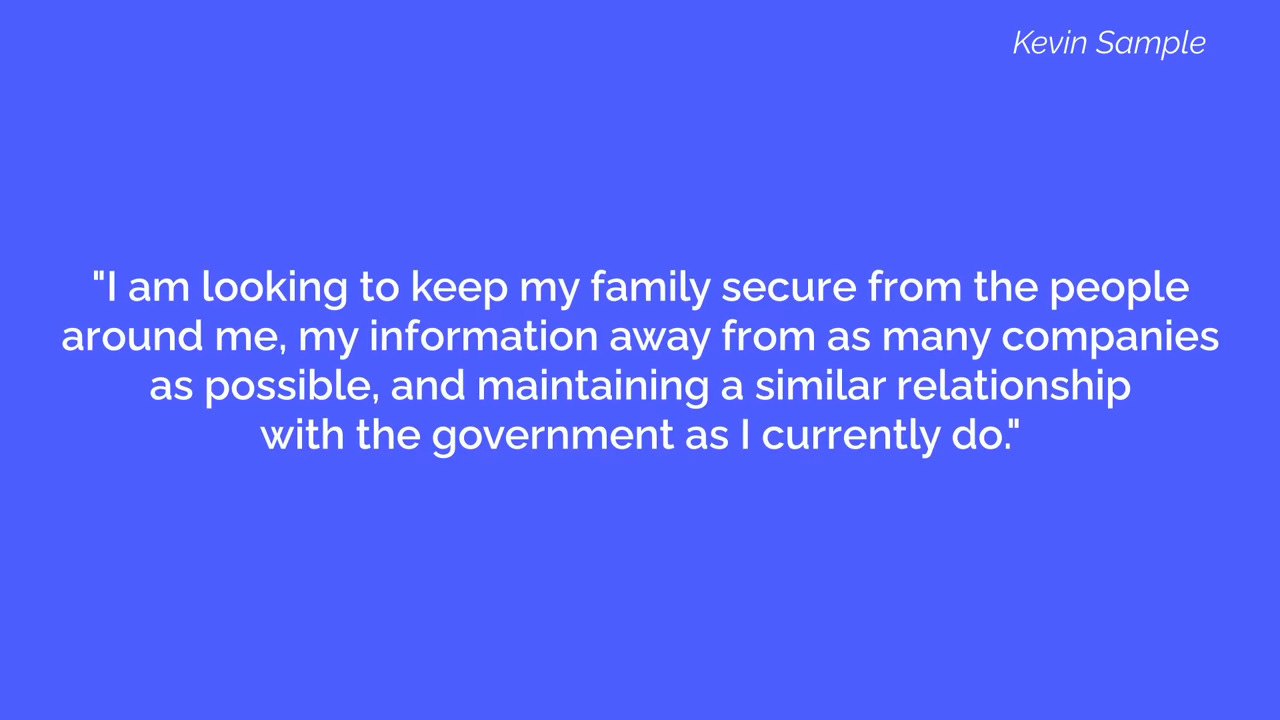
Write a general sentence describing your whole threat model.
Congratulations! you now have a threat model, you can use this threat model to cross-reference all your decisions going forward so you know which services to use and which you should cut off!
Watch this video if you’re still confused! 👇
For businesses and organizations:
A business or organization should be asking these four questions to be able to properly implement a threat model:
What are we working on?
What can go wrong?
What are we going to do about it?
Did we do a good enough job?
Check out the Threat Modeling Manifesto if you’re interested in implementing a threat model for your company.
Common mistakes to avoid:
Focusing too much on security without considering usability: While security is important, it's also important to consider the usability of the system. If the security measures make it too difficult to use the system, users may find workarounds that negate the security benefits.
Assuming all threats are equal: Not all threats are equal in terms of their impact. It's important to prioritize the threats and focus on the ones that are most likely to occur and have the greatest impact.
Failing to update the threat model: Threat modeling is not a one-time activity. It should be updated regularly to ensure that new threats are accounted for and existing threats are mitigated effectively.
Tools and processes for threat modeling:
For advanced folks, companies and developers: (you should probably skip this)
Microsoft Threat Modeling Tool: This tool is designed to help users identify threats and vulnerabilities in their software applications.
OWASP Threat Dragon: This is an open-source, web-based threat modeling tool that helps users create and analyze threat models.
IriusRisk: This tool allows users to create threat models and generate reports based on the identified risks.
P.A.S.T.A: This is a process for threat modeling that stands for Process for Attack Simulation and Threat Analysis. It is a structured approach for identifying and analyzing potential threats to an application or system.
STRIDE: This is a mnemonic for Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege. It is a framework for identifying and categorizing threats.
DREAD: This is a mnemonic for Damage, Reproducibility, Exploitability, Affected users, and Discoverability. It is a framework for assessing the severity of identified threats.
Take a look at this awesome paper by the Carnegie Mellon University and this great article by The OWASP® Foundation extensively covering the advanced available methods and processes for threat modeling.
— So there you have it! Threat modeling may sound scary and serious, but it's just like playing a game of 'What if?' with your computer. Just remember to keep your tinfoil hat handy and your sense of humor intact, and you'll be ready to tackle any threat that comes your way. And who knows, maybe one day you'll even get a medal for your excellent threat modeling skills. Or at the very least, a pat on the back from your IT department. Stay safe out there!